
How Long Can A Pokemon Stay In A Gym, How long can a Pokemon stay in a gym without berries, 1.26 MB, 00:55, 640, Ask About SPORTS, 2020-08-07T21:37:34.000000Z, 19, How long can a pokemon stay on a gym? | Pokemon GO Wiki - GamePress, pokemongo.gamepress.gg, 1440 x 1280, png, pokemon gym stay gamepress pokemongo, 20, how-long-can-a-pokemon-stay-in-a-gym, KAMPION
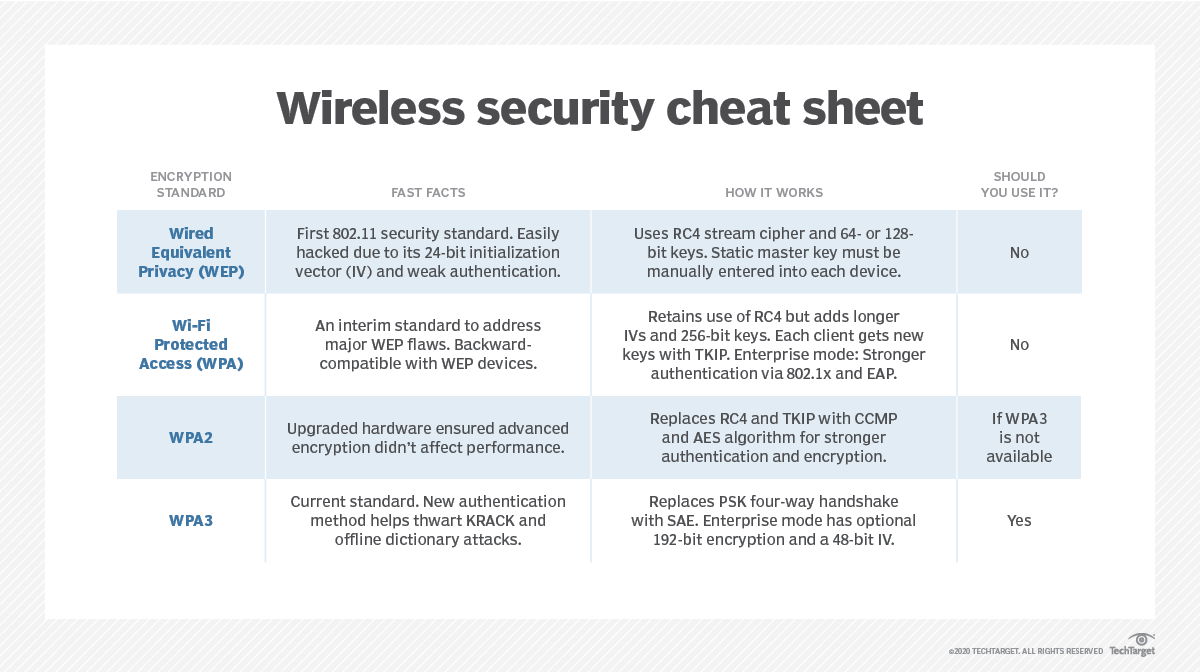
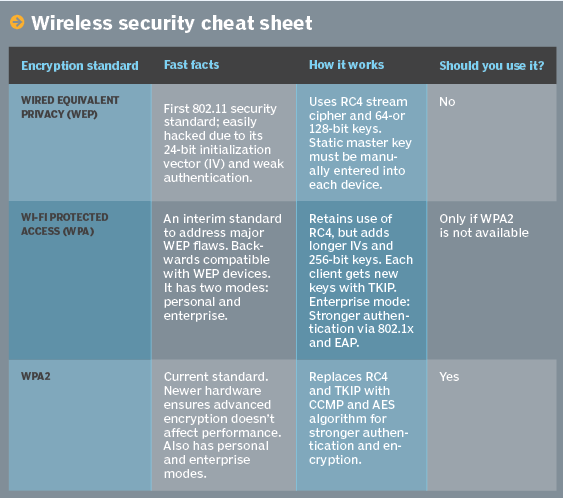
Wpa3 may become the new mandatory standard in the future. You should be using this option. Aes (based on the rjiandael algorithm) is a block cipher (the “s. Which encryption protocol below is used in the wpa2 standard?
Which eap protocol creates an encrypted channel between the client authentication server and the client, and uses microsoft windows logins and. Here openvpn tcp certainly refers to the one working over tcp tunnel. The temporal key integrity protocol (tkip) encryption technology uses a mic value that is what length? Which encryption protocol below is used in the wpa2 standard? Which of the following choices is not one of the four types of packets used by eap? Which encryption protocol below is used in the wpa2 standard? Some wireless aps do not support wpa3, however. In that case, the next best option is wpa2, which is widely deployed in the enterprise. It uses key lengths of 256 bits, which makes it virtually impenetrable to brute force attacks (on present computing power).
WPA-2 encryption and integrity check Message integrity check (MIC): AES

Wi-Fi Security Evolution - How we ended up in WPA3?

WPA-2 encryption and integrity check Message integrity check (MIC): AES

WPA-2 encryption and integrity check Message integrity check (MIC): AES

WEP vs WPA vs WPA2 | Difference between WEP,WPA,WPA2
Wireless security protocols: The difference between WEP, WPA, WPA2
[802.11] Wi-Fi Security Concepts - NXP Community
![Which Encryption Protocol Below Is Used In The Wpa2 Standard? [802.11] Wi-Fi Security Concepts - NXP Community](https://community.nxp.com/t5/image/serverpage/image-id/126824i0286F5EB61185BBA/image-size/large?v=1.0&px=999)
KRACK: The Massive Wi-Fi Security Flaw
IEEE 802.11i-2004

CMC3P22-P03-1001232F: Differences between IEEE 802.11i, IEEE 802.11r

EmoticonEmoticon